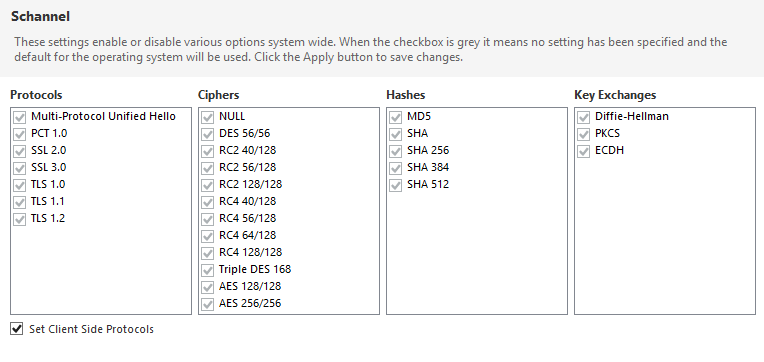
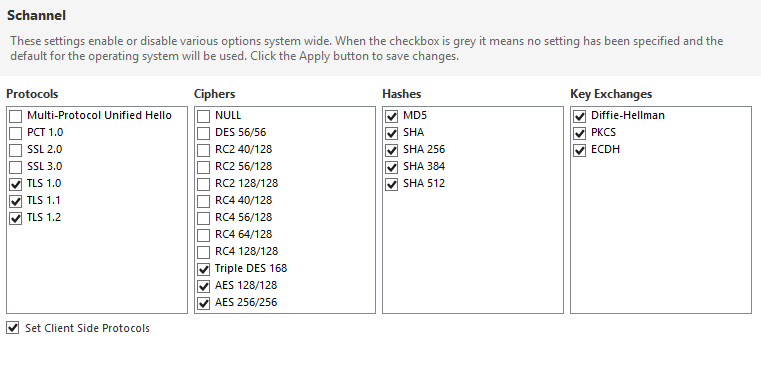
If your servers still support TLS 1.0 or older obsolete cryptographic protocols (SSL, PCT, …) for communication over the network , you should act asap!
Description:
SSL 3.0 and older protocols, now also TLS 1.0 are vulnerable to man-in-the-middle attacks, risking the integrity and authentication of data sent between a website and a browser. Disabling TLS 1.0 and older protocols support on your server is sufficient to mitigate this issue! These obsolete protocols should be Disabled before public deadline – June 30, 2018 for SSL/Early TLS Migration. Ups.. Yes , this date is gone already :\….and also Windows Servers 2016 by default support these protocols !!!
The deadline -June 30, 2018 it is not my invention. This deadline was scheduled by The PCI Security Standards Council which is a global open body formed to develop, enhance, disseminate and assist with the understanding of security standards for payment account security. Probably after this date, this vulnerability could be reported to ICT teams by their local security team. – https://blog.pcisecuritystandards.org/4-things-to-know-about-pci-dss-in-2018
Technical Details:
Secure Sockets Layer (SSL) and early versions of Transport Layer Security (TLS) are no longer considered secure forms of encryption. It is critically important that organizations upgrade to a secure version of TLS – such as TLS v1.2 or higher – as soon as possible and disable any fallback to SSL/early TLS.
Many PCI DSS requirements require the use of ‘strong cryptography’ as defined in the PCI DSS glossary. After 30 June 2018 SSL/early TLS should not be used as a security control to meet any PCI DSS requirements attempting to demonstrate strong cryptography.
Default Windows Server 2012 R2, Server 2016 configuration is below:
Recommend configuration (change requires server restart):
Screenshots from tool – https://www.nartac.com/Products/IISCrypto
IISCrypto is very good alternative way how to set secure sonfiguration on your server, when you do not want to do it directly in Registry.
Microsoft sources about this topic: